As a user moves from client to client, TermSecure logs them in and instantly reconnects to the existing terminal server sessions and virtual desktops while programs follow and instantly appear on screen, ready to use. When the user walks away, they are automatically logged out and the client returns to its original function.
Identify yourself at a TermSecure enabled device using an RFID proximity card (short or long range), a USB flash key, or login manually. Combine authentication methods and greatly increase security.
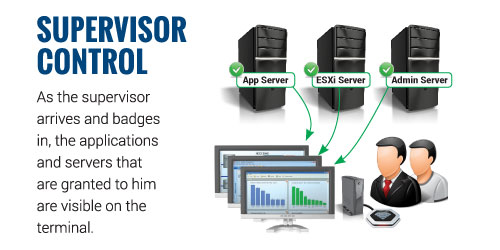
Administrators control user access to terminals and applications through group permissions and terminal scheduling. Limit a specific user to a weekly, daily or hourly schedule or disable the terminal itself at any time you choose.
Drop our ActiveX control into your applications and you can program in terminal and user specific functionality, including session switching, event logging, and terminal status and management.
Prevent a single unauthorized access to your systems and you might also be preventing a downtime event that more than pays for this software. Save a minute or more each time you access applications from a client over the life of your systems and now you have money in the bank.